
Update 18.08.2011 — PIB Release says, “The Government proposes to bring out a legislation that will provide protection to individuals in case their privacy is breached through unlawful means. For the purpose it is working on ‘Right to Privacy’ Bill. The drafting of the legislation is at a very preliminary stage and details of the legislation are yet to be finalized.” (Ministry of Personnel, Public Grievances & Pensions, Right to Privacy Bill, Release ID :74743)
This post contains a summary of the third working draft of the Privacy Bill, 2011 dated 19th April, 2011 which aims to create a statutory right to privacy in India (download here). This note also contains an analysis on the significant features of the enactment. I will be posting comments on its provisions in the coming weeks.
It is important to note that the Privacy Bill, 2011 which as per media reports is to be introduced by the government in the next session of parliament has not been formally made public or a consultation process has been followed in its drafting (Prashant writes on the drafting process here). In case of any questions or comments please contact me at mail@apargupta.com. I would like to acknowledge the work put in by an Akansha Nehra, an intern at my office in helping me with this note.
The readability of this post is somewhat hampered due to a lack of formatting which is not carried forward from Mircrosoft Word to WordPress. To counter this I am embedding a PDF towards the end of the post.
- 1. The Privacy Bill, 2010 : a broad level view
a) It creates a statutory Right to Privacy by means of a broad definition and then creates specific of protections for it. Recognising the Right to Privacy not to be absolute, the Bill identifies various privacy breaches that are permitted. In the Bill, certain prohibited acts are also identified for which civil remedies as well as criminal sanctions are created.
b) The government interception and telephone tapping mechanism is changed moderately from the existing system. The modification is with respect to several procedural safeguards which are put into place to avoid unauthorised and unnecessary tap orders.
c) A regulatory mechanism is created through the Data Protection Authority of India. It will exercise supervision over private parties which will engage in the collection and storage of personal data.
d) Further, in the system suggested, the Bill identifies specific officers/position holders in various entities (that may be involved in various breach of the right) who shall be held responsible, in case of any wrong act or any default.
e) Disputes under the Bill will be referred to the Cyber Appellate Tribunal which has been set up under the Information Technology Act. These disputes are primarily in the nature of claims by individuals against private data controllers.
- 2. INDEX: CONSTITUENTS OF THE BILL
The Bill contains fifteen chapters and ninety four sections and has been divided in the following manner
ChapterSection NumberNameI1, 2PreliminaryII3Right to PrivacyIII4–13Privacy of Communication and Prohibition from its InterceptionIV14–23Procedure for Interception of CommunicationV24Prohibition of Surveillance and its RegulationVI25–26Use of Photographs, Fingerprints, Body samples of persons, DNA samples, and other samples taken at Police StationVII27–28Health Information PrivacyVIII29–31Privacy relating to DataIX32–42Obligation and Procedure for collecting or processing or using or disclosing dataX43–48ResiduaryXI49–62The Data Protection Authority of IndiaXII63–66Grants, Funds, Accounts and Audit and Annual ReportXIII67Settlement of DisputesXIV68–84Offences and PenaltiesXV85–94Miscellaneous
- 3. SCOPE OF RIGHT TO PRIVACY
- Section 3(1) provides for the Right to Privacy and stipulates that every individual has a right to privacy and the same is subject to any law for the time being in force or an order of the Court. It is important to bear that this acts as an carve out since any the privacy right under the Privacy Bill which is created is subject to existing laws. The privacy rights are in addition to existing laws and not in derogation to them. Hence any existing law which is in conflict with any of the mandates of the Privacy right under Section 3 enjoys preference and legal validity.
- Interestingly though, several laws have been made exempt from the privacy right under Section 90. Though ordinarily these laws would have been exempt as per Sec. 3(1), the draftsman seems to be leaving nothing to chance by excluding statutes such as the Right to Information Act; The Prevention of Corruption Act; from the ambit of the privacy right. It is also important to comment on a saving provision under Section 89, which makes space for any nature of right to be also included in the scope of the statutory right of privacy, which may be subsisting already.
- Section 3(2) provides for an inclusive definition by providing for 12 kinds of manifestations of privacy, which are listed below:
a) Confidentiality of communication
b) Confidentiality of private/ family life
c) Protection of honor and good name
d) Protection from search, detention, or exposure of lawful communication between and among individuals
e) Privacy from surveillance
f) Confidentiality of banking and financial transactions
g) Confidentiality of medical and legal information
h) Protection from identity theft (criminal, financial, identity cloning, medical)
i) Protection from use of photographs, fingerprints, DNA samples, and other samples taken at police stations or other places
j) Privacy of health information
k) Protection of data relating to an individual.
4. PRIVACY OF COMMUNICATION AND INTERCEPTION
- After creating the right to privacy under Sec. 3(2), the Bill provides prescriptions for the confidentiality of communication and safeguards for their interception under Chapters III and IV of the Bill. It is important to bear that the privacy right in India is essentially a set of procedural safeguards. The more safeguards the stronger the privacy right. The expanse of the legal provisions recognises that the most prevalent privacy breach is with respect to the interception of communications.
- The terms, “confidentiality” has been defined as, “a process of sharing facts, ideas, opinions, thoughts, and information through speech, writing, gestures, sound, images, signals or pictures, graphs, symbols, diagrams between two or more individuals through telephonic conversations, radio messages, electronic mode (including internet or satellite) or postal letter or any other mode”. Interception further has been defined as, “undertaking the stopping of transmission of any communication, or interception or detention thereof (including tapping of the telephone conversation or copying of data)”. The interception safeguards are explained in a tabular form below:
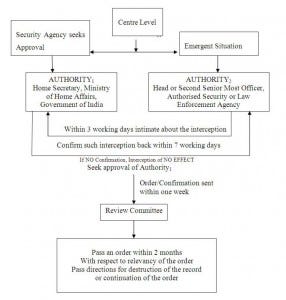
FeatureProvisionRule of PrivacyPrivacy is not AbsoluteSection 4 stipulates the right of any citizen of India, to have his communication protected from interception. But, the same is not an absolute right and is limited by the provisions of the Bill under discussion.Condition [Procedure]There are two conditions precedent to intercept a communication legally.Firstly, the conditions under Section 5(2) of the Indian Telegraph Act, 1885 must be satisfied. Secondly, an order must be issued by an officer not below the rank of Home Secretary [Ministry of Home Affairs, Government of India] and the Home Secretaries of the State Governments which records the satisfaction of these conditions.ApplicationThe provision applies to any surveillance. It also applies to activities incidental to interception.ExceptionAn exception is created with respect to the authorities that can make such an order, and it is permitted that this power can be delegated to another officer of a stipulated rank.Further, in emergent situation (the kinds have been specified) interception can be made without an order under Section 5, after obtaining subsidiary approvals from the Central and the State governments (stipulated officers).Secondary ProcedureUnder Section 6(2), such subsidiary approval giving authority has to within 3 working days place the order before an appropriate authority and seek confirmation. Such authority should send a confirmation within 7 working days.Deemed DiscontinuanceIf no confirmation is received, then the interceptions will have to be discontinued and any further interception will require permission of the Union Home Ministry or the State Home Secretary, as the case maybe.System EmployedThe system proposed by the Bill identifies two bodies. One is the Requisitioning Service Agency (Government) and the other is the Service Provider (the Telecommunications Company or the ISP). Each has been required to appoint nodal officers and the transaction of exchange of any information collected shall occur only between them. Strict guidelines are provided for such exchange, as the same has been asked to follow a method of exchanging appropriate acknowledgement letters, etc.Liability of Service ProviderFurther, the Service Providers have been placed with responsibility, as they have to every fifteen days submit a list of authorizations, to the Security agencies for confirmation of authenticity of the directions received by them. Further, stipulations are provided with respect to secrecy, maintenance of data, destruction of records etc. This will check unauthorized tap orders purportedly emanating from government as noticed in the recent decision of Amar Singh v. Union of India WP(C) 39/2006 (available at http://www.indiankanoon.org/doc/1082001/) .Liability of Requisitioning Security AgencyThe authority must maintain the records of such orders, the intercepted communication, etc. The Order must contain appropriate details with respect to the communication being intercepted, the authority permitting the same, etc.Validity of OrderThe Bill provides that the option of intercepting a communication should be limited to that much as is necessary,[1] and that the said permission will cease to have effect on the expiry of 2 months, unless renewed.[2] It also provides that if any other alternative mechanism exists to collect the said information, it should be used instead.Review CommitteeThe order or confirmation should be tabled before the concerned Review Committee, within one week, which should look into the relevancy of each order on its own motion.
The interception mechanism sought to be created by the Privacy Bill, 2011 is represented in a process flow below:
5. OTHER MANIFESTATIONS OF RIGHT TO PRIVACY
Along with the provisions for the breach of communications privacy, the Privacy Bill, 2011 also prescribes various safegaurds for the other forms of privacy which are mentioned under Sec. 3(2). These forms of privacy as well as the permissible breaches are presented in the table below:
Kind of RightStipulations and LimitationsUse of materials collected at a Police StationNature of MaterialThe right identified herein is in the light of use of materials like photographs, fingerprints, DNA samples, of any citizen of India.UserThe use of such material by another person is the ambit of the said provision and includes Government officer as well.Nature of Prohibited UseThis is applied in context of revealing material (one’s personal or private information) in public which will adversely affect his right to privacy, such as to amount to a civil wrong.Permitted UseThis rule is relaxed by stating that such materials maybe collected with the consent of the individual or if it is needed under any other law (such as the Code of Criminal Procedure, 1973).Procedure to be taken care ofThis is implied to be used for the purposes stipulated (by means of law or consent) and after such use should be destroyed or returned.Health Information PrivacyNature of InformationThis rule applies to collection of health information in respect of an individualUserThe use that is being analysed under this provision is by another person, including a Government officer as well.Nature of Prohibited UseThis is applied in context of revealing such health information in public which will adversely affect his right to privacy, such as to amount to a civil wrong.Nature of Permitted UseThe use that is permitted is by collecting with his consent or under any other law.Procedure to be taken care ofThis is implied to be used for the purposes stipulated by his consent and after such use should be destroyed or returned.Without ConsentThe information collected by said means, the nature of use, duration of retaining of such information, and manner of disposal shall be as per the law.Conditional UseSuch information, collected by whatever means, should not be revealed to the publicPrivacy relating to DataCategory of UserThis provision covers such person which has a place of business in India or if does not have a business in India, but has a Data Using Equipment in IndiaPersons not having business in India, shall nominate a representative for collecting/using/processing/disclosing data.Nature of Permitted UseMay be collected with his consent or under the said Bill or any other lawNature of Use ExcludedIf the processing of data meant for transmission outside India is by using equipment located in India, solely for the purpose of such transmission, it is permitted.Violation of right to privacyAny disclosure by a person of information (as stipulated under this kind) of a person without his consent or not in accordance with any law, shall be violation of the Right to Privacy.Exceptions11 exceptions to this right have been provided for under which a person may collect/process/use/disclose, under Section 30.Nature of Collectable Personal DataData is a part of the public record, or has been made public by said individualIndividual has consented on collection of such data from an alternative source (other than public records)Restriction on Collection of Personal dataIf it is collected directly, appropriate details must be disclosed to the individual.Restriction on Processing of DataIt has been provided that the data must be collected for the purpose for which permission has been sought and in a fair, appropriate and lawful manner.Right of a Data Subject in situation of Data ProcessingIn case of data processing for an Unsolicited Commercial Communication, the data subject has the right to make an application to the Data Controller to discontinue such processing.FeaturesNo individual can be coerced to disclose certain details as a pre-condition to the provision of goods or services, in addition to information that is needed to functionally provide it.A separate category of sensitive personal data has been identified and the use of such data requires distinct permissions, etc.Further there are specific provisions for Data Retention, Data Security and its Breach, Data Access and its correction as wellResiduaryProvisionsChapter X acts as the Residuary manifestations of an individual’s right to privacy, and provides for acts of maintenance of records, use and disclosure of information, etc.
- 6. BODIES UNDER THE PRIVACY BILL, 2011
- Data Protection Authority of India
The Data Protection Authority of India has been set up as a regulatory body to administer the Privacy right created under the Privacy Bill, 2011. The Bill provides for 13 functions that the Authority performs. These include, ensuring compliance with the provisions with respect to data under the Bill by the bodies to which it applies, monitor developments in science and technology and policy to keep them upbeat with the rights, maintain appropriate network with respect to data controllers and the Registry, to attempt to increase and spread literacy in this aspect and involve public and also includes its power to investigate any data breaches, etc. The Authority has power to pass three types of orders, those seeking, disclosure, inquiry or inspection.
2. National Data Controller Registry
This is in the form of an online database in order to facilitate the efficient and effective entry of particulars by data controllers. A data controller has the permission to process any personal data of any data subject, only after the data controller has made an entry in the registry. The database shall contain details of the purpose with which a data controller seeks to process any data. This shall be available to public free of cost. Appropriate data protection protocols and correction procedure are proposed to be prepared.
3. Cyber Appellate Tribunal
Civil disputes such as claims for compensation under the Privacy Bill, 2011 are proposed to to be reffered to the Cyber Regulations Appellate Tribunal which is established under Section 48 of the Information Technology Act, 2000. The jurisdiction of the Tribunal conferred under Section 67 of the Privacy Bill, 2011 confers two types of jurisdictions. Firstly, original jurisdiction with respect to any dispute arising between an individual and a data controller. Secondly appellate jurisdiction with respect to any appeal from any order or direction or decision of the Authority [Data Protection Authority of India]. It is of interest that this Appellate Tribunal through this Bill will be given original jurisdiction where earlier it only sat as a court of appeal.
- 7. OFFENCES AND PENALTIES
SectionProvisionsOffenceOffenderPenaltyOther DetailsImprisoment uptoFine uptoBoth68Chap. III and IVUnauthorised Interception of Communicationundertakes interception of any Communication5 yrs1 lakhBoth-69Disclosure of Intercepted Communicationintercepts or has any personal information3 yrs50,000/-BothExceptions70Chap. VIIIObtaining personal information on False Pretencerequests for such information on false pretence-5 lakhs-From any person or Officer of the Government71Chap. III and IVViolation of conditions of License to Service ProvidersService ProviderSuspend/Revoke licenseConditions pertaining to maintenance of secrecy and confidentiality of information and unauthorised interception of communicationWithout Prejudice to liability under license or any other law72Chap. VUndertaking surveillance in contravention of Section 24undertakes the surveillance5 years1 lakhBothFor each surveillance73Chap. VIIIDisclosure of other Personal InformationAny officer or Employee of the Service Provider or the Government (who has possession of or access to Records of the Service Provider or Government-5 lakhs-Records which contain Individually identifiable Information or personal informationInformation is such that disclosure is prohibited under this Bill or any other law or which affects the right of an individualThe offender knows disclosure is prohibited and wilfully discloses to one not entitled to know the same74Chap. VItaking and using of photographs, fingerprints, DNA samples in publictakes such material and uses them5 years1 lakhBothof any Citizen of India75Chap. VIINot permitted declaration of Health Informationdiscloses it6 months1 lakhBothInformation with respect any citizen of India (in contravention of provisions of this Bill)
SectionWith respect toOffenceOffenderPenalties1st Time offenceSecond or Subsequent Offence [Extend to]Continuing Offence [For every day]77Chapter XIContravention of Directions of the Data AuthorityViolator1 lakh2 lakhs2 lakhs (for every day)78Chapter VIIIData TheftPerson who (intentionally and without authorisation from Data Subject or Data Controller) acquires or gains access to any personal data7 lakhs10 lakhs-79(1)Chapter IXUnauthorised Processing of personal dataAny person processing any personal data in contravention of Chapter II1 lakh5 lakhs [For each subsequent offence]-79(2)Any person processes personal data without first making an entry in the Registry5 lakhs — 80Chapter XContravention of Chapter X-1 lakh5 lakhs [For each subsequent offence]-
- 8. REMEDIES UNDER THE BILL
The Bill recognises the right to privacy, in its various ambits. Hence, it also provides what all can be pursued in case of its violation. The following remedies are available to an aggrieved person.
a) Compensation
Any person who suffers damage can claim for compensation any damage caused to him by any data controller, under section 76. The damage must be due to any contravention on part of the data controller. Here it is sought to be clarified that the amounts described in the table are with respect of penalties. These penalties operate as fines. They are intended to deter illegal conduct. However, compensation which is provided under Sec. 76 acts as a remedy aims to restitute the loss of the person complaining of damage.
b) Civil Remedies
Section 84 provides that the individual, whose right to privacy has been adversely affected, may bring a civil action against such persons have caused such violation. This is addition to any criminal proceedings existing against such person (violator).
c) Criminal Remedies
Chapter XIV provides for various offences that may be committed under the nature of right provided for under this bill. But, the rider is provided for under Section 82, where any Court may take cognizance of offence under this Bill, solely on the compliant made by the Authority.
[1]Section 9
[2] Section 10(1)
[ipaper id=58794641]